Securing Your Digital Perimeter:
Why MFA for VPNs Is Non-Negotiable in 2025
The cybersecurity battlefield has evolved—and in 2025, relying on passwords alone to protect your virtual private network (VPN) is akin to defending a fortress with a cardboard shield. As cybercriminals harness artificial intelligence (AI) to launch faster, smarter, and more devastating attacks, multi-factor authentication (MFA) has transitioned from a “best practice” to a business-critical requirement. Here’s why your organization’s survival depends on it.
The New Reality: AI-Powered Threats Are Rewriting the Rules
Cyberattacks in 2025 aren’t just frequent; they’re inevitable. Bad actors now deploy AI-driven tools that learn, adapt, and strike with surgical precision:
- AI-Generated Phishing: Attackers use generative AI to mimic executives’ writing styles, create fake video calls, and craft emails so convincing that even vigilant employees fall prey.
- Brute Force Evolution: Machine learning algorithms crack weak passwords in seconds, bypassing traditional lockout mechanisms.
- Credential Harvesting at Scale: Dark web marketplaces overflow with stolen credentials, many scraped from decades-old breaches. Without MFA, these credentials become instant gateways to your network.
Real-World Impact:
A recent breach at a global logistics firm began with a single compromised VPN login. Attackers used AI to map the network, exfiltrate sensitive contracts, and deploy ransomware—costing the company $8.2 million in recovery and legal fees.
Why VPNs Are Ground Zero for Cyberattacks
VPNs remain the backbone of remote work, cloud access, and third-party vendor connections. But this omnipresence makes them a prime target:
- Remote Work Expansion: Hybrid workforces mean more entry points for attackers.
- Supply Chain Vulnerabilities: A hacker breaching a vendor’s VPN accounts can infiltrate your systems undetected.
- Ransomware’s Favorite Path: Almost 30% of ransomware attacks in 2024 originated via VPNs lacking MFA.
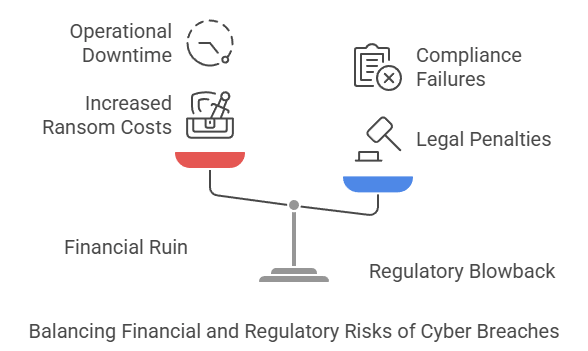
The Consequences of Complacency:
- Financial Ruin: The average ransomware payout in 2024 has surged to $4.26 million (AUD) almost a $1 million increased from 2023, not including downtime or reputational harm.
- Regulatory Blowback: Laws like America's updated Privacy Act penalize companies for “preventable” breaches, including failures to implement MFA.
- Operational Collapse: A single breach can disable operations for weeks, alienate clients, and erode stakeholder trust.
MFA: The Unbreakable Lock on Your Digital Doors
Multi-factor authentication adds layers of defence that AI struggles to overcome. Even if a password is stolen, attackers still need:
- Something You Have (e.g. a mobile device with an authenticator app).
- Something You Are (e.g. biometric verification like a fingerprint or facial scan).
Top MFA Methods for 2025:
- Phishing-Resistant FIDO2 Keys: Physical USB/NFC devices that block credential theft.
- Phishing-Resistant Pass Key Authentication: Setup on a hardware device like a mobile phone.
- Authenticator One Time Password: Apps like Microsoft Authenticator or Google Authenticator.
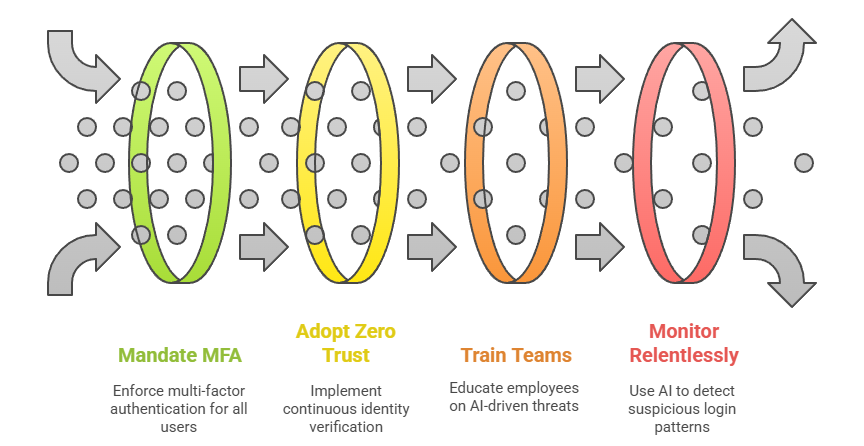
Act Now or Risk Annihilation
- Mandate MFA for All VPN Access: No exceptions—contractors, executives, and IT admins alike must comply.
- Adopt Zero Trust Frameworks: Treat every login attempt as a potential threat. Verify identities continuously.
- Train Teams to Spot AI-Driven Social Engineering: Run simulations using USecure or Seven Labs to test employee knowledge of fake information.
- Monitor Relentlessly: Deploy AI-powered threat detection to flag suspicious login patterns in real time.
The Bottom Line
In 2025, MFA isn’t about staying ahead, it’s about surviving. Cybercriminals have an army of AI tools at their disposal, and every unprotected VPN login is a ticking time bomb. The question isn’t whether your business should implement MFA, but whether you can afford the fallout if you don’t.
Your Next Step:
Contact us today and demand MFA enforcement. The cost of delay could be existential.